Services We Offer
At Red Dragon Security, we provide comprehensive penetration testing services designed to identify and address vulnerabilities in your systems before malicious actors can exploit them. Our expert team delivers thorough assessments including internal/external network, web application, and physical security testing. We offer tailored solutions to meet your specific needs, ensuring robust protection for your digital assets. Partner with us to stay ahead of threats and secure your infrastructure with confidence.
Internal Network Testing
Our Internal Network Testing service simulates real-world attacks from within your organization to uncover vulnerabilities that could be exploited by insiders or attackers who have breached your perimeter defenses. We meticulously assess your internal network’s security, identify weak points, and provide actionable recommendations to fortify your defenses. Ensure your internal infrastructure is as secure as your external perimeter
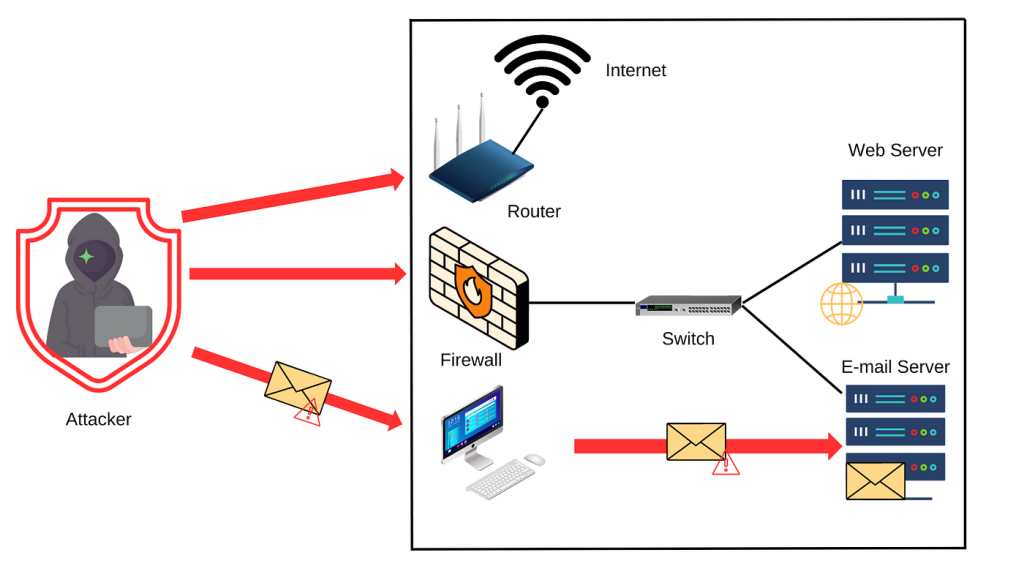
External Network Testing
Our External Network Testing service is designed to expose vulnerabilities that could be exploited by attackers from outside your organization. We perform rigorous assessments of your public-facing infrastructure, including servers, firewalls, and network configurations, to identify weaknesses before they can be exploited. Our detailed analysis and actionable insights will help you strengthen your defenses against external threats and safeguard your digital assets from potential breaches.
Web Application Testing
Our Web Application Testing service dives deep into your online applications to identify and address security vulnerabilities that could be exploited by attackers. We rigorously evaluate your web applications for common and advanced threats, including SQL injection, cross-site scripting (XSS), authentication and authorization weaknesses. By uncovering these issues, we provide actionable insights to fortify your applications and safeguard sensitive data.

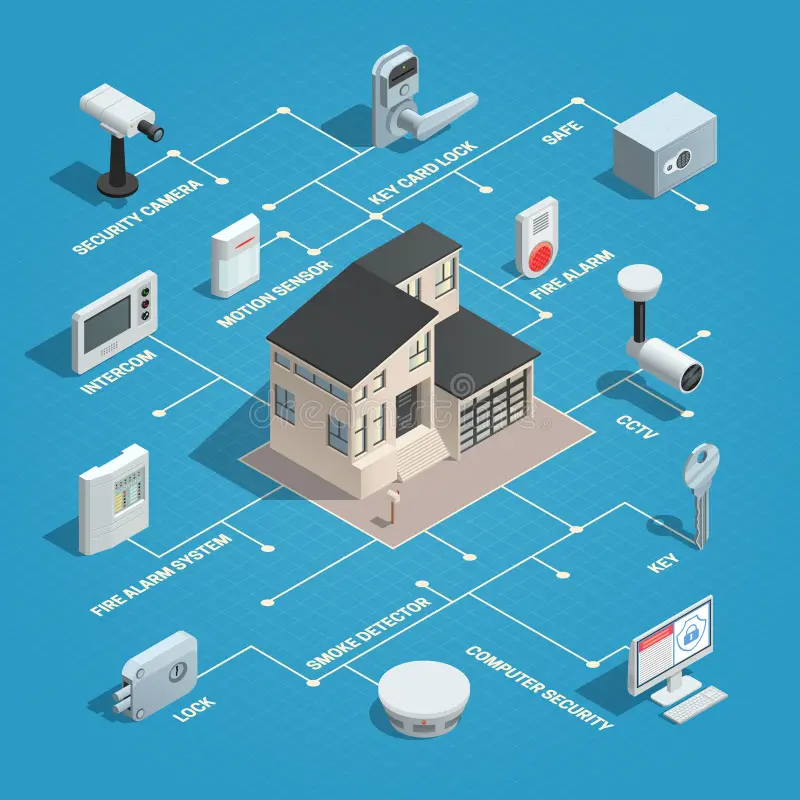
Physical Testing
Our Physical Security Testing service evaluates the effectiveness of your physical access controls and security measures. We simulate real-world scenarios to identify vulnerabilities in areas such as entry points, surveillance systems, and security personnel protocols. By uncovering potential weaknesses, we help you enhance your physical security posture and protect sensitive areas from unauthorized access.

